Protect your expanding IoT ecosystem from emerging threats with SecuEdge’s comprehensive security solutions designed specifically for the unique challenges of IoT environments.
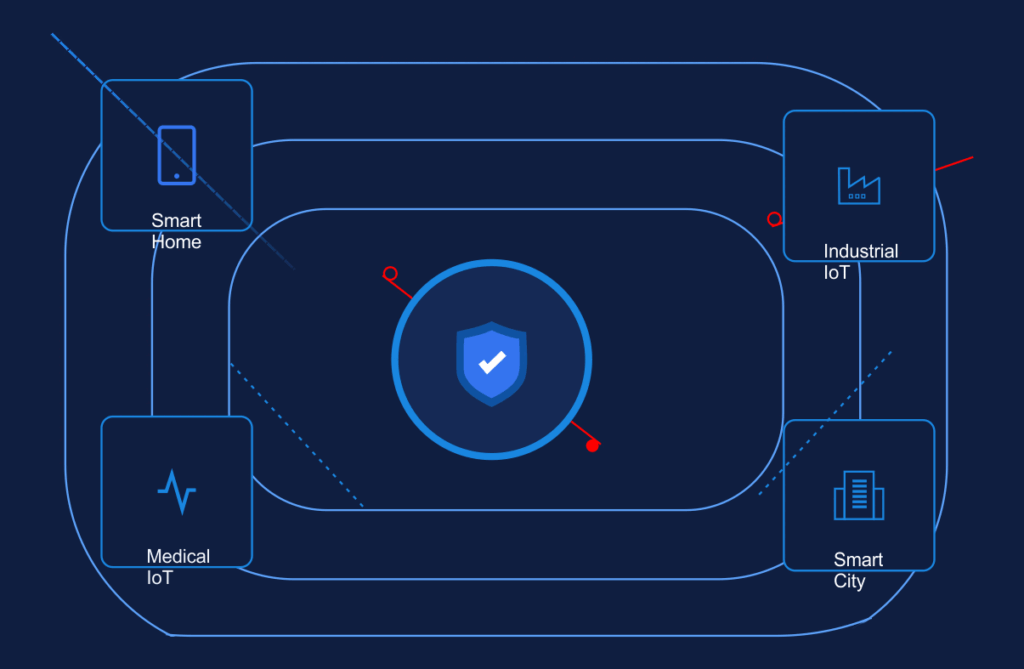
IoT environments face distinct security challenges that traditional cybersecurity approaches cannot adequately address.

Many IoT devices connect using insecure protocols and may lack encryption, creating easy entry points for attackers.

IoT ecosystems include diverse devices with different operating systems, creating complex security management challenges.

Many IoT devices lack the processing power and memory to run traditional security software or regular updates.

Devices shipped with default passwords and unnecessary open ports create significant security vulnerabilities.

Many IoT devices implement poor authentication mechanisms, making it easy for unauthorized users to gain access.

IoT devices often collect sensitive data about users and environments, creating privacy and compliance risks.
IoT environments face distinct security challenges that traditional cybersecurity approaches cannot adequately address.

Attackers compromise large numbers of IoT devices to create botnets for DDoS attacks or cryptocurrency mining

Intercepting communications between IoT devices and management systems to steal data or inject malicious commands

Targeting vulnerabilities in device firmware to gain persistent access and control over IoT devices

Attackers compromise large numbers of IoT devices to create botnets for DStealing sensitive data collected by IoT sensors and devices for espionage or financial gainDoS attacks or cryptocurrency mining
Recent IoT Security Breach
Critical infrastructure breach with significant impact
A large manufacturing company's industrial IoT sensors were compromised through unpatched vulnerabilities in their network controllers.
Attackers gained control of critical production systems, causing $4.7M in downtime and compromising proprietary manufacturing data.
After implementing SecuEdge's IoT security solution, the company established device authentication, network segmentation, and continuous monitoring, preventing similar attacks.
Financial Loss
Devices Affected
Production Downtime
Data Compromised
Modern threats require modern defenses that go beyond traditional security measures.
Ensure only authorized devices can connect to your network with robust authentication mechanisms and digital certificates
Isolate IoT devices in separate network segments to prevent lateral movement and contain potential breaches
Identify abnormal device behavior and potential threats with AI-powered monitoring and analytics
Centrally manage device configurations, updates, and security policies across your entire IoT ecosystem
End-to-end visibility of all IoT devices and connections
Reduced attack surface through network segmentation
Real-time threat detection and automated response
Simplified compliance with regulatory requirements
Our IoT security solution provides the essential capabilities needed to protect your connected devices and infrastructure.

Establish and verify the identity of every IoT device connecting to your network

Encrypt all data transmitted between IoT devices, gateways, and cloud platforms

Isolate IoT devices in separate network segments to limit lateral movement of threats

Deploy and manage digital certificates for strong device authentication and encryption

Detect anomalous device behavior using AI-powered analytics to identify potential threats

Deploy authenticated and encrypted firmware updates to maintain device security

Identify and remediate security vulnerabilities across your IoT ecosystem

Block malicious connections and activities targeting your IoT devices

Generate detailed reports to demonstrate compliance with industry regulations
Our IoT security solutions adapt to the unique requirements of different industries and use cases.

Protect critical industrial control systems, manufacturing equipment, and operational technology from cyberattacks while ensuring production continuity.

Secure building automation systems, HVAC controls, access control systems, and other smart building technologies against cyber threats.

Protect critical industrial control systems, manufacturing equipment, and operational technology from cyberattacks while ensuring production continuity.

Secure connected urban infrastructure including traffic systems, utilities, lighting, environmental sensors, and public safety systems.

A user receives a phishing email with a malicious document containing a zero-day exploit that’s unknown to traditional antivirus.We begin with a comprehensive inventory of your IoT ecosystem, identifying all devices, connections, and potential vulnerabilities.

When the document is opened, it attempts tBased on the assessment, we develop a tailored security architecture that addresses your specific IoT security requirements and constraints.o exploit a vulnerability and execute a fileless payload that evades traditional detection.

The attack attempts to exploit PowerShellOur experts deploy the IoT security solution, starting with critical security controls and gradually expanding protection across your entire ecosystem. to establish persistence and connect to a command and control server.

We thoroughly test the security implementation to ensure all controls are functioning properly and providing the expected protection.

After deployment, we continuously monitor your IoT security posture, providing regular updates and optimizations to address evolving threats.
Find answers to common questions about our IoT security solutions and how they can help protect your connected devices.

Next-generation firewall protection for enterprise-grade security. Defending networks against advanced cyber threats.
© 2025 SecuEdge. All rights reserved.